The OWASP top 10
The OWASP top 10 is a list of the most common vulnerabilities in web applications. The list is periodically updated on the basis of the developments of the past year.
What is OWASP?
OWASP is an organization committed to a safer world. OWASP stands for Open Web Application Security Project.
What does the OWASP top 10 consist of?
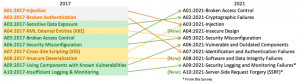
The most common vulnerabilities according to OWASP are:
- Broken Access Control – The application does not protect sensitive parts, such as a non-logged-in user who can view sensitive information or a user can change another person’s data
- Cryptographic Failures – Failure to encrypt confidential information or not properly. With the GDPR it is mandatory to protect sensitive data, during transmission and sometimes when storing (such as medical data or credit card data)
- Injection – attackers can inject malicious code. These include, for example, XSS, SQL injections and path traversal
- Insecure Design – The system architecture is not designed to be secure
- Security Misconfiguration – The system is configured insecurely
- Vulnerable and Outdated Components – The system uses standard components that contain known vulnerabilities. This ensures that the standard known vulnerabilities can also be found in custom applications
- Identification and Authentication Failures – Login vulnerabilities allow attackers to gain access to accounts, including lack of protection against brute-force attacks and allowing passwords like “admin/admin”
- Software and data integrity failures – The system assumes that data received can be trusted, for example an update file, without checking whether it has not been modified
- Security Logging and Monitoring Failures – Attackers can go about their business without anyone noticing
- Server Side Request Forgery (SSRF) – The application makes a request that it shouldn’t.
What’s new in the OWASP top 10 2021 update?
The OWASP top 10 has recently been updated. The order has changed and a number of categories have been merged, creating space for new vulnerabilities. The big newcomer (albeit in 10th place) is Server-Side Request Forgery (SSRF). Curious about what SSRF is all about? We explain it in our knowledge base article.
Am I safe if I do not have any vulnerabilities from the OWASP top 10?
Not necessarily. The top ten are the most common web application vulnerabilities. This means that the vulnerabilities for other assets such as domain controllers, printers or workplaces can be very different. In addition, they are the 10 most common, not the only 10.
Is the Website Security Check tested for the OWASP top 10?
Yes, all CyberAnt products test for the OWASP top 10. In addition, the Website security check also checks for vulnerabilities that are not in the OWASP top 10.
Does a Pentest check for the OWASP top 10?
Yes, the pentest checks for the OWASP top 10, but also for other known vulnerabilities. In addition, we look for vulnerabilities that have not yet been found by anyone, the so-called zero days.

