User settings for AWS security audits
Some of the security auditing on AWS environments takes place automatically. For this we need an API user with the right settings. The user we create has read-only privileges on the settings so we can review them. In this article, we explain how to configure this user.
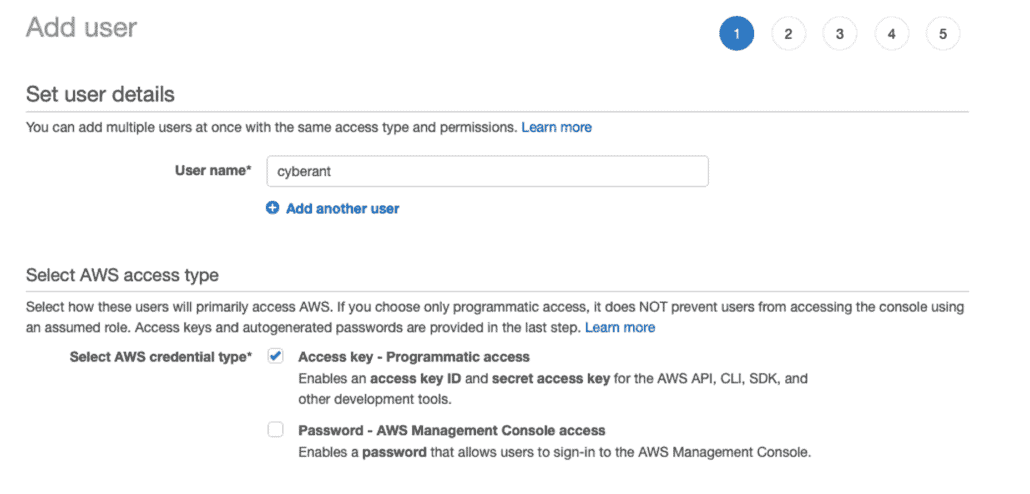
Create a user named “cyberant,” and give it the SecurityAudit policy. You do this by logging in with an AWS admin account and going to the IAM console. Then under “Access management” there is the “users” button. Then click on “Add users.”
For the username, enter “cyberant,” and click the “Programmatic access” function.
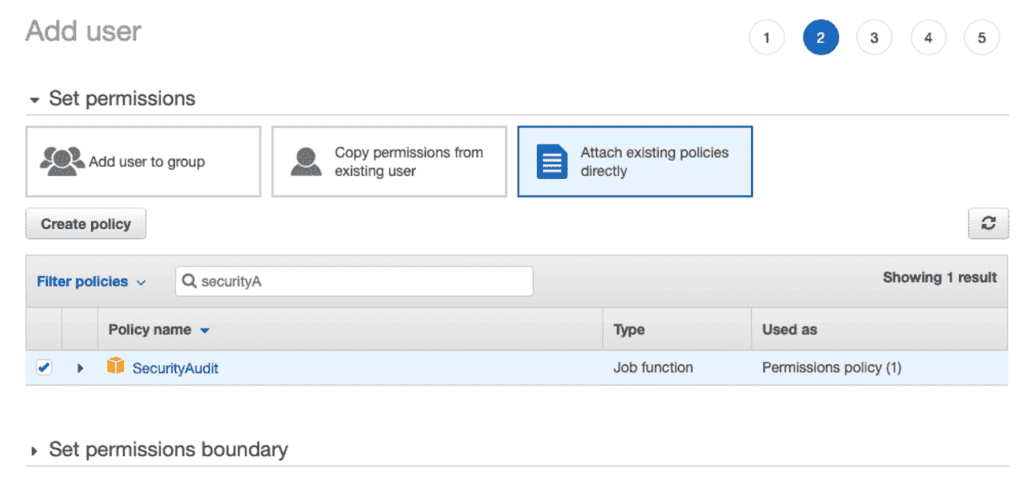
Click “Attach existing policies directly” and select the “SecurityAudit” policy.
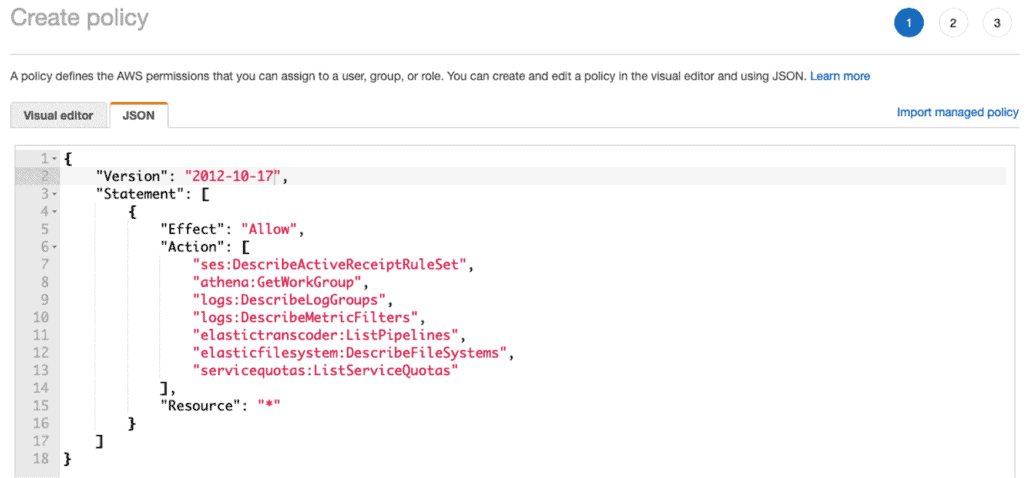
Unfortunately, not all the permissions we need are included in this policy, for this reason we are creating a new policy. Click on “Create policy” and then on JSON. Give it the following value:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ses:DescribeActiveReceiptRuleSet",
"athena:GetWorkGroup",
"logs:DescribeLogGroups",
"logs:DescribeMetricFilters",
"elastictranscoder:ListPipelines",
"elasticfilesystem:DescribeFileSystems",
"servicequotas:ListServiceQuotas"
],
"Resource": "*"
}
]
}
Enter any tags (optional) and click review. Name the policy “SecurityAuditPlus” and save it.
Return to the previous screen, click the refresh button, and add the new policy “SecurityAuditPlus.” Two policies should now be selected.
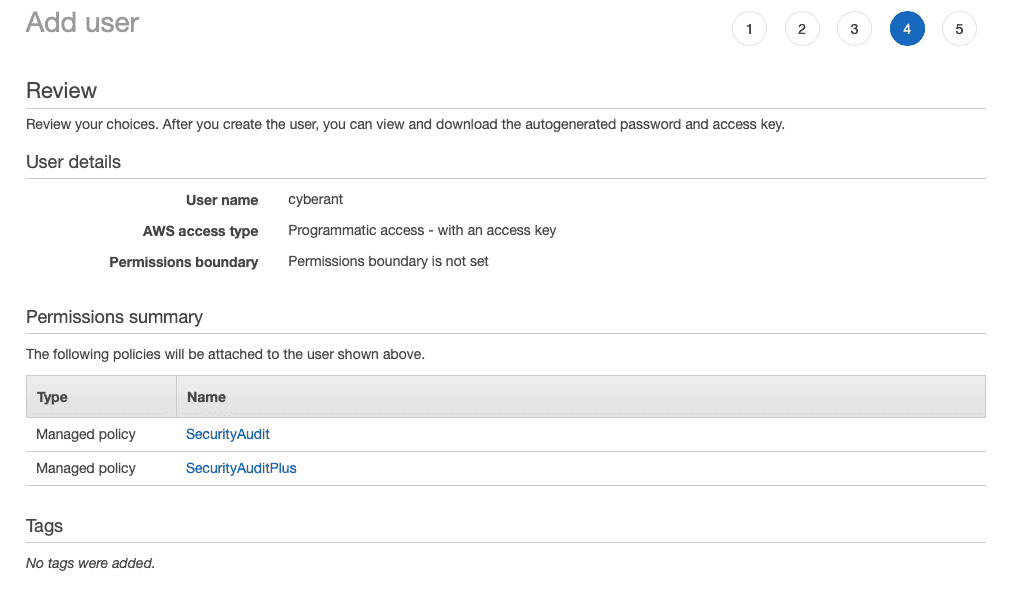
Continue to create the user, at the review page the following should be set:
Add the user. Ensure that the Access key ID and Secret access key are stored carefully and securely. These are needed during the audit.