What is Server-side request forgery (SSRF)?
Server side request forgery (SSRF) is an attack where the server makes a request that it shouldn’t. It is part of the OWASP top 10 on place 10.
Example of server side request forgery
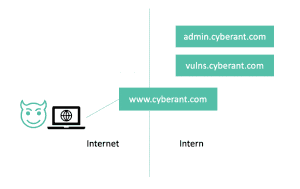
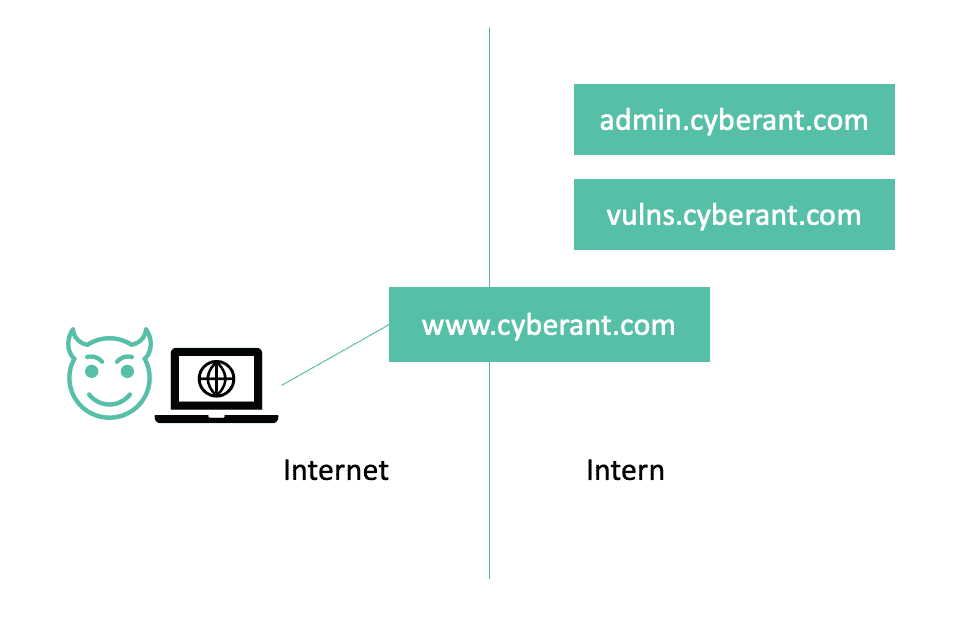
In the example below, the attacker can only get to the website www.cyberant.com. The attacker wants to attack the website admin.cyberant.com, which is not reachable via the internet. Therefore, the only option to do this is through the website.
Of course, the attacker can try to take over the website completely, but if this doesn’t work (and there is a good chance of course), there is another option: SSRF.
Suppose we have the following request:
POST /vulns/1/info HTTP/1.0
Content-Type: application/x-www-form-urlencoded
Content-Length: 123
vulnApi=https://vulns.cyberant.com/
The server will now retrieve information from vulns.cyberant.com. However, the API is free to fill in, so the attacker can freely modify this:
POST /vulns/1/info HTTP/1.0
Content-Type: application/x-www-form-urlencoded
Content-Length: 123
vulnApi=https://admin.cyberant.com/launch/missles
The website will now make a request to admin.cyberant.com instead of vulns.cyberant.com. Depending on the implementation of the website, the result of the admin application may or may not be displayed. If the request is made, but the result is not displayed, we speak of a blind SSRF vulnerability.
How can you prevent SSRF?
SSRF vulnerabilities can be prevented by letting the client do the request itself. This should of course be possible, in the above example the user cannot reach the vulns application. Another option is to whitelist or preconfigure the URL so that the attacker cannot modify it.